What is the Gartner Magic Quadrant?

Anastasios Arampatzis
It can take time to choose how to invest your limited funds. Making the correct investments in the cybersecurity technology that protects and supports your strategic business ambitions takes work. A complicated equation that balances people, processes, and technology must be solved to ensure your firm’s success.
If you want to provide high-quality security services in your business, one of the pillars you must master is the Gartner Magic Quadrant. This market research is essential to understand how well security vendors carry out their ambitions. Additionally, it will assist you in choosing the appropriate technology for your business.
What is the Gartner Magic Quadrant?
For more than 40 years, Gartner has been providing tools like their renowned Gartner Magic Quadrant to assist businesses in making quicker and more informed decisions. Mention the Magic Quadrant to any security and IT professional, and they will immediately understand what you mean.
Gartner Magic Quadrants provide insight into a market’s direction, maturity, and participants through visual glimpses, in-depth analysis, and practical advice. A Gartner Magic Quadrant results from extensive market research and provides a broad overview of the relative positions of the market’s players. A Magic Quadrant lets you rapidly determine how well technology suppliers are carrying out their stated visions and performing compared to Gartner’s market view by applying a graphical treatment and a consistent set of evaluation criteria.
The report visually represents the analyzed market in a two-dimensional matrix. The matrix evaluates vendors based on their Completeness of Vision and Ability to Execute.
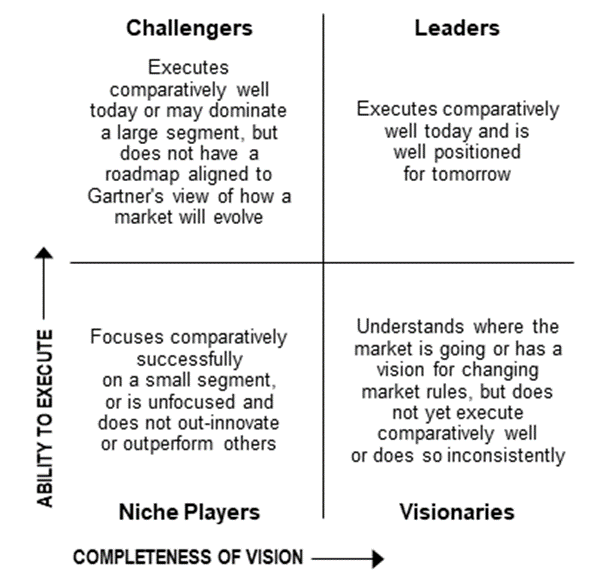
Figure 1: Source Gartner, https://www.gartner.com/en/research/methodologies/magic-quadrants-research
The Magic Quadrant charts cybersecurity businesses compared to other essential players in a specific field (i.e., Access Management or Backup and Restore) and is typically published on a 12-month cycle. It is important to remember that a Magic Quadrant is an examination of vendors compared to predetermined assessment criteria rather than a review or endorsement of a product. Gartner may no longer publish specific Quadrant reports as technology advances. In this instance, the Data Loss Prevention report’s publication ceased after 2018.
For a particular investment opportunity, businesses should use a Gartner Magic Quadrant as a starting point to understand the technology suppliers they should consider. According to Gartner, concentrating only on the leaders’ quadrant isn’t necessarily the best strategy. Market challengers should also be taken into consideration for many reasons. And a niche player could better serve corporate demands than a market leader. Everything depends on how well the provider matches the objectives of the company.
How do Gartner Magic Quadrants work?
A Magic Quadrant is a visual representation showing the competitive positioning of four types of technology providers in the cybersecurity market. This is especially useful in a rapidly growing market where each provider has distinct differences that set them apart.
- Niche Players – A company situated in the lower left quadrant specializes in a particular section of the cybersecurity market and lacks a clear strategy for expanding and implementing more qualifications. A niche focus is not necessarily a negative approach, especially if your security requirements are highly specific.
- Visionaries – Visionary companies strongly understand where the market is going or have creative ideas for reshaping how technology is perceived. However, they may not have yet demonstrated these ideas in practice.
- Challengers – Challenger vendors possess sound organizational frameworks and can maintain pace with contemporary cybersecurity requirements. However, they often lack the foresight to provide the solutions that customers will require in the future.
- Leaders – Located in the upper right quadrant, we have the Leaders. These companies have proven their ability to meet current standards and have a track record of past successes and a clear plan for meeting future standards.
The interactive capabilities in the Magic Quadrant reports allow businesses to tailor their view of the Magic Quadrant to their needs, requirements, and priorities. Companies can create a customized Magic Quadrant graphic by changing the weightings given to each evaluation factor. These specialized reports can then be distributed for internal analysis and well-informed decision-making.
The interactive Magic Quadrant combines the Peer Insights customer reviews and the professional judgment of Gartner’s analysts. Security professionals can read and assess what other security professionals say about the solutions they have implemented in their organization on the User Review tab.
More than just market analysis; an awareness tool
Businesses can gain valuable insights by contextualizing a Gartner Magic Quadrant according to their specific industry, region, and company size. This approach offers additional perspectives that can have a significant impact on decision-making. Magic Quadrants can help businesses:
- Get a timely education on the various technology providers in the cybersecurity industry and how well they are equipped to meet the needs of businesses now and in the future.
- Learn about the competitive positioning and strategies cybersecurity providers use to enhance prospects’ security.
- Compare a vendor’s strengths and challenges with the business needs and goals.
Cybersecurity professionals and business leaders can use the Gartner Magic Quadrant to analyze its elements and plan short- and long-term strategies. This will help them overcome business challenges, protect growth opportunities, and make secure investments in a constantly changing security environment.

Anastasios Arampatzis is a retired Hellenic Air Force officer with over 20 years’ worth of experience in managing IT projects and evaluating cybersecurity. During his service in the Armed Forces, he was assigned to various key positions in national, NATO and EU headquarters and has been honoured by numerous high-ranking officers for his expertise and professionalism. He was nominated as a certified NATO evaluator for information security.
Anastasios’ interests include among others cybersecurity policy and governance, ICS and IoT security, encryption, and certificates management. He is also exploring the human side of cybersecurity – the psychology of security, public education, organizational training programs, and the effect of biases (cultural, heuristic and cognitive) in applying cybersecurity policies and integrating technology into learning. He is intrigued by new challenges, open-minded and flexible.
Currently, he works as a cybersecurity content writer for Bora Design.
Tassos is a member of the non-profit organization Homo Digitalis.
